How To Prevent Cell Phone Phishing Attacks
Discover ways to stop cellphone phishing assaults with easy suggestions and finest practices. Shield your knowledge and keep secure from cellular scams.

There are numerous forms of assaults that we’re uncovered to for the time being, amongst which we are able to spotlight the well-known and most used assault, phishing assaults.
Now, right here is the primary query: can we shield ourselves from these assaults? The reply is sure, as we are able to use completely different strategies to keep away from these assaults on our cellular gadgets.
Phishing in voice calls

Phishing makes an attempt primarily based on voice calls, also called “vishing”, are extra direct than SMS since these attackers have the newest applied sciences, reminiscent of caller ID, distant automated dialers, numbers primarily based on space codes, or entry to our private data.
That’s why we should always at all times watch out with one of these name since professional corporations won’t ever ask you for personal knowledge over the cellphone, simply as they might not do it via electronic mail.
Phishing assault via messages (SMS)
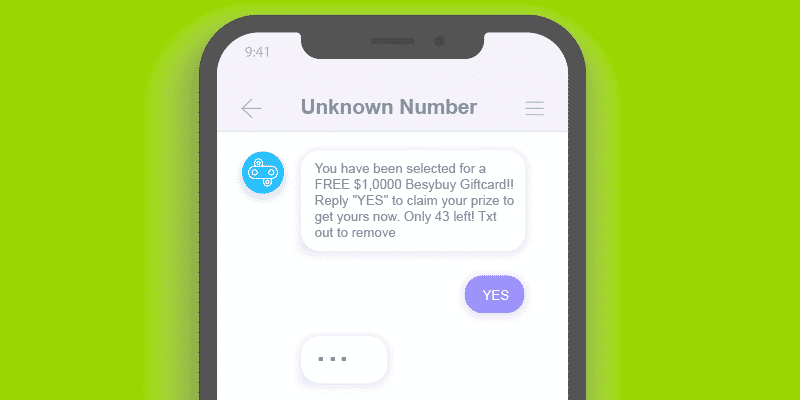
Using SMS has existed for years, and its performance hasn’t modified a lot, because it focuses on capturing the sufferer’s consideration with profitable incentives.
On this, the attackers hunt for checking account and bank card knowledge and entry credentials to platforms, cryptocurrencies, or PayPal accounts, amongst different issues. After which, this data may be bought for a great revenue on the Darkish Internet.
The very best we are able to do to keep away from this isn’t to click on on any hyperlink that forces us to behave in a rush.
Phishing by cellphone quantity

These assaults by cellphone numbers are among the many standard phishing scams and give attention to the safety system of financial institution accounts with two-factor authentication.
The attackers gather private data reminiscent of cellphone numbers, date of start, and so on., to switch our SIM to a different firm and obtain the financial institution particulars, which is taken into account monetary fraud.
As the method of change takes a number of hours or days, if we discover that the cellphone cannot carry out primary capabilities reminiscent of calling or sending SMS, we might discover ourselves in one in every of these instances, so it might be handy to contact the corresponding operator to keep away from one of these assault.

In these assaults, attackers can pose as celebrities, buddies, or household to deceive us. Therefore, whether or not it’s a reliable contact or not, we should stay alert and by no means share our knowledge or data via social networks with different contacts in any state of affairs.
How to Fix Google Maps Draining Battery on Android
So, what do you concentrate on this security tutorial? Share all of your views and ideas within the remark part under.